On Whitebox Wireless Security Assessments
Performing a white box wireless security assessment can be really useful to an organization if you have access to diverse datasets. The type of data you can get from this methodology is very different from what you might get from a black box wireless penetration test, but that's a good thing. I actually recommend alternating between methodologies for each wireless assessment, so that you get the full spectrum of wireless vulnerability data. Below are some ideas on white box wireless security assessment methodology. Most, if not all of this can be done remotely, if you do your rogue AP checking using the wireless controller.
Datasets
Now let's talk about how to use the datasets to produce the deliverables. Hopefully, vulnerability scans are being run every month on all hosts, providing data which can be used for a wireless assessment. If not, you may need to run custom scans. If you're using Nessus, just filter by host and export all vulns pertaining to the wireless controllers and a sampling of access points in PDF format. Next, tend to the Windows hosts. Search by plugin name containing krack and export the results as a PDF. Here are some example Nessus plugins for KRACK:
Before getting into wireless history though, you may want to check the following plugin for any computers that were connected to the organization's guest/public WiFi during the time of the scan, as this presents risk to the organization:
To get the full wireless network history of each Windows host, however, use this plugin:
To get the data you'll need, be sure to export 66350 as PDF>Custom>Vulns>By host. This will allow you to get detailed information you will need for your report. (Exporting as CSV seems to truncate a lot more information than PDF.) Once you have the PDF, open it and copy/paste all the text to a plain text file. You may want to check for a few places where Nessus may have truncated the output, deleting any uninteresting SSIDs that have "Description [...]" (without quotes) under them. Then use grep to extract the computer name, SSID and date last connected to the SSID from the text file:
grep "Netbios Name:\|SSID : \|DateLastConnected : " pastedfrompdf.txt
Copy all the text from the text file into Excel twice - once in column A and once in column B. What you want to do now, is move the cells around to the correct places, en masse. This can be done the following way:
Magic! You now have column B populated with only computer names. Now you need to get a column that has only DateLastConnected entries:
Now we have some pretty good data. You can search and replace (replace with nothing) the prepended text that is in each cell, if you like, and create appropriate column headers. Consider also using Excel to remove duplicates that are matched in both the SSID and computer name. You may find that there are a small amount of entries with no DateLastConnected for whatever reason, but this is still some really useful information overall. You can use filtering to search for guest or public and possibly see some pretty interesting results. It may be that employees are connecting to the guest wireless to get Facebook, for instance, thereby endangering the organization. Your report should recommend using black/whitelisting of SSIDs with Group Policy to solve this. Try also filtering the date column by the year for fresh results, with something like: /2018
Next, let's look at rogue access points. I really think that in most cases, you can do 99% of your rogue access point auditing remotely, instead of walking around scanning with antennas. That's because most enterprise wireless controller solutions offer robust rogue access point features. For instance, Cisco's RLDP (Rogue Location Discovery Protocol) does some pretty cool stuff to try to detect if a rogue AP is connected to the wired LAN. If you can get access to the GUI of a Cisco wireless controller, you should be able to find the "rogue summary" and note the number of "rogues on wired network". Very useful stuff, and saves a lot of legwork. Due to the limitations of RLDP, you should also consider looking through the entire list of of rogue AP's (even those not detected on the wired network), to see if there is anything of interest.
Lastly, I recommend doing some traditional capturing/cracking with the traditional tools, and creating a corresponding report. You should be able to perform the handshake capture remotely, if you ship a wireless USB NIC to the target site and use a Kali VM.
Traditional wireless attack tools:
Please understand, I don't recommend anyone just dump a bunch of PDFs and spreadsheets on stakeholders. It's important to review the data manually before delivering, and provide thoughtful analysis. Go through each dataset and decide if it is relevant, presentable and most importantly, actionable! Consider presenting highlights in a slide deck and presenting to stakeholders.
Happy cracking!
Datasets
- Nessus Scans
- Windows computers
- Wireless controllers
- Access Points
- Checking for Rogue APs within the wireless controller GUI
- Traditional handshake cracking
- Infrastructure Vulnerability Scan Report
- KRACK Report
- SSID History Report (for determining if org computers are connecting to the org's guest wifi)
- Rogue Access Point Report
- Handshake Cracking Report
Now let's talk about how to use the datasets to produce the deliverables. Hopefully, vulnerability scans are being run every month on all hosts, providing data which can be used for a wireless assessment. If not, you may need to run custom scans. If you're using Nessus, just filter by host and export all vulns pertaining to the wireless controllers and a sampling of access points in PDF format. Next, tend to the Windows hosts. Search by plugin name containing krack and export the results as a PDF. Here are some example Nessus plugins for KRACK:
- 103746 (plugin ID) - Windows 7 and Windows Server 2008 R2 October 2017 Security Updates (KRACK)
- 103870 - Intel - Wireless Driver Wi-Fi Protected Access II (WPA2) Multiple Vulnerabilities (KRACK)
Before getting into wireless history though, you may want to check the following plugin for any computers that were connected to the organization's guest/public WiFi during the time of the scan, as this presents risk to the organization:
- 25197 - Windows Wireless SSID (WMI)
To get the full wireless network history of each Windows host, however, use this plugin:
- 66350 - Microsoft Windows Wireless Network History
To get the data you'll need, be sure to export 66350 as PDF>Custom>Vulns>By host. This will allow you to get detailed information you will need for your report. (Exporting as CSV seems to truncate a lot more information than PDF.) Once you have the PDF, open it and copy/paste all the text to a plain text file. You may want to check for a few places where Nessus may have truncated the output, deleting any uninteresting SSIDs that have "Description [...]" (without quotes) under them. Then use grep to extract the computer name, SSID and date last connected to the SSID from the text file:
grep "Netbios Name:\|SSID : \|DateLastConnected : " pastedfrompdf.txt
Copy all the text from the text file into Excel twice - once in column A and once in column B. What you want to do now, is move the cells around to the correct places, en masse. This can be done the following way:
- Filter column B by: ssid :
- Highlight all of column B
- Right click > Clear contents
- Filter column B by: DateLastConnected :
- Highlight all of column B
- Right click > Clear contents
- Unfilter column B
- Highlight blanks using: Home > Find and select > Go to special > Blanks
- Press the = key
- Click on cell B1
- Type control-enter
Magic! You now have column B populated with only computer names. Now you need to get a column that has only DateLastConnected entries:
- Insert a column between columns A and B
- Copy column A to the new column B
- Filter column B by: ssid :
- Highlight all of column B
- Right click > Clear contents
- Filter column B by: Netbios Name:
- Highlight all of column B
- Right click > Clear contents
- Unfilter column B
- Move all the cells in column B up one row
- Filter column A by ssid :
- Copy/paste all the filtered cells from all 3 columns to a new sheet
Now we have some pretty good data. You can search and replace (replace with nothing) the prepended text that is in each cell, if you like, and create appropriate column headers. Consider also using Excel to remove duplicates that are matched in both the SSID and computer name. You may find that there are a small amount of entries with no DateLastConnected for whatever reason, but this is still some really useful information overall. You can use filtering to search for guest or public and possibly see some pretty interesting results. It may be that employees are connecting to the guest wireless to get Facebook, for instance, thereby endangering the organization. Your report should recommend using black/whitelisting of SSIDs with Group Policy to solve this. Try also filtering the date column by the year for fresh results, with something like: /2018
Next, let's look at rogue access points. I really think that in most cases, you can do 99% of your rogue access point auditing remotely, instead of walking around scanning with antennas. That's because most enterprise wireless controller solutions offer robust rogue access point features. For instance, Cisco's RLDP (Rogue Location Discovery Protocol) does some pretty cool stuff to try to detect if a rogue AP is connected to the wired LAN. If you can get access to the GUI of a Cisco wireless controller, you should be able to find the "rogue summary" and note the number of "rogues on wired network". Very useful stuff, and saves a lot of legwork. Due to the limitations of RLDP, you should also consider looking through the entire list of of rogue AP's (even those not detected on the wired network), to see if there is anything of interest.
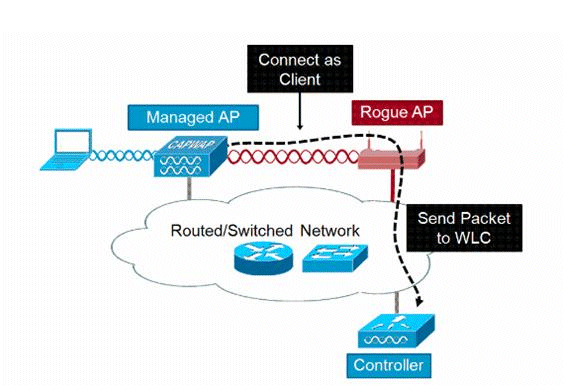 |
| Cisco's Rogue Location Discovery Protocol |
Lastly, I recommend doing some traditional capturing/cracking with the traditional tools, and creating a corresponding report. You should be able to perform the handshake capture remotely, if you ship a wireless USB NIC to the target site and use a Kali VM.
Traditional wireless attack tools:
- airmon-ng
- airodump-ng
- aireplay-ng
- aircrack-ng
- hashcat
- hashcat-utils
Please understand, I don't recommend anyone just dump a bunch of PDFs and spreadsheets on stakeholders. It's important to review the data manually before delivering, and provide thoughtful analysis. Go through each dataset and decide if it is relevant, presentable and most importantly, actionable! Consider presenting highlights in a slide deck and presenting to stakeholders.
Happy cracking!


Comments
Post a Comment