Using Error Codes When Password Spraying Citrix NetScalers
In a previous blog post, I outlined some of my successes and failures with password spraying against Citrix NetScalers. It can be difficult to get a parsable response from NetScalers, meaning that it is challenging to know if a given credential set resulted in a successful login or a failed login. I've recently had more success with this type of attack though, due to new information I've discovered.
I noticed recently that some NetScalers respond to logon attempts with a cookie which contains an error code, though it wasn't immediately possible to interpret the meaning of the code. The error codes I observed in responses were as follows:
NSC_VPNERR=4001
NSC_VPNERR=4009
This led me to dig around further, at which time I discovered the following XML file on the target:
https://example.com/logon/themes/Default/resources/en.xml
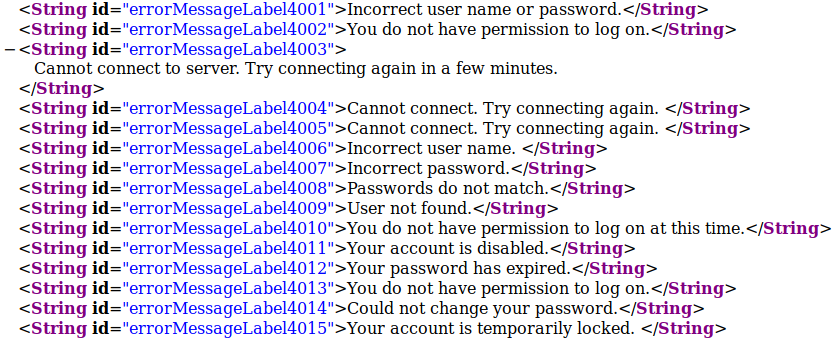
I was happy to find that this file contains the definitions of the error codes:
Using these codes I was able to confirm that invalid usernames yielded 4009, allowing me to determine valid usernames and confirm the account naming convention. Once I refined my attack, I was able to crack credentials using Burp Suite Intruder, by observing that valid usernames yielded the following response:
HTTP/1.1 302 Object Moved
Location: /cgi/setclient?wica
Set-Cookie: <redacted>
POSTLOGINFLAGS : 1
Set-Cookie: <redacted>
Server:NS11.0.70.16
Connection: close
Content-Length: 0
Cache-control: no-cache, no-store
Pragma: no-cache
Content-Type: text/html
This was a notable breakthrough for me regarding password spraying against Citrix NetScalers, which had previously been problematic and is now quite trivial. I'm not yet able to confirm which versions of the NetScaler behave in this way, but the header in the response seems to indicate the version is 11.0.70.16. I'll continue to test this during penetration test projects and hope to determine exactly which versions this attack is successful against. Feel free to chime in with your findings, as well.
I noticed recently that some NetScalers respond to logon attempts with a cookie which contains an error code, though it wasn't immediately possible to interpret the meaning of the code. The error codes I observed in responses were as follows:
NSC_VPNERR=4001
NSC_VPNERR=4009
This led me to dig around further, at which time I discovered the following XML file on the target:
https://example.com/logon/themes/Default/resources/en.xml
I was happy to find that this file contains the definitions of the error codes:
Using these codes I was able to confirm that invalid usernames yielded 4009, allowing me to determine valid usernames and confirm the account naming convention. Once I refined my attack, I was able to crack credentials using Burp Suite Intruder, by observing that valid usernames yielded the following response:
HTTP/1.1 302 Object Moved
Location: /cgi/setclient?wica
Set-Cookie: <redacted>
POSTLOGINFLAGS : 1
Set-Cookie: <redacted>
Server:NS11.0.70.16
Connection: close
Content-Length: 0
Cache-control: no-cache, no-store
Pragma: no-cache
Content-Type: text/html
This was a notable breakthrough for me regarding password spraying against Citrix NetScalers, which had previously been problematic and is now quite trivial. I'm not yet able to confirm which versions of the NetScaler behave in this way, but the header in the response seems to indicate the version is 11.0.70.16. I'll continue to test this during penetration test projects and hope to determine exactly which versions this attack is successful against. Feel free to chime in with your findings, as well.


Found this resource helpful...
ReplyDeletehttps://www.citrix.com/blogs/2014/06/11/enhanced-authentication-feedback/